Been fighting this malware junk all week so I wanted to add few notes for the next person.
For WordPress, Wordfence worked best for me with all check-boxes under ‘Scans to include’ being selected.
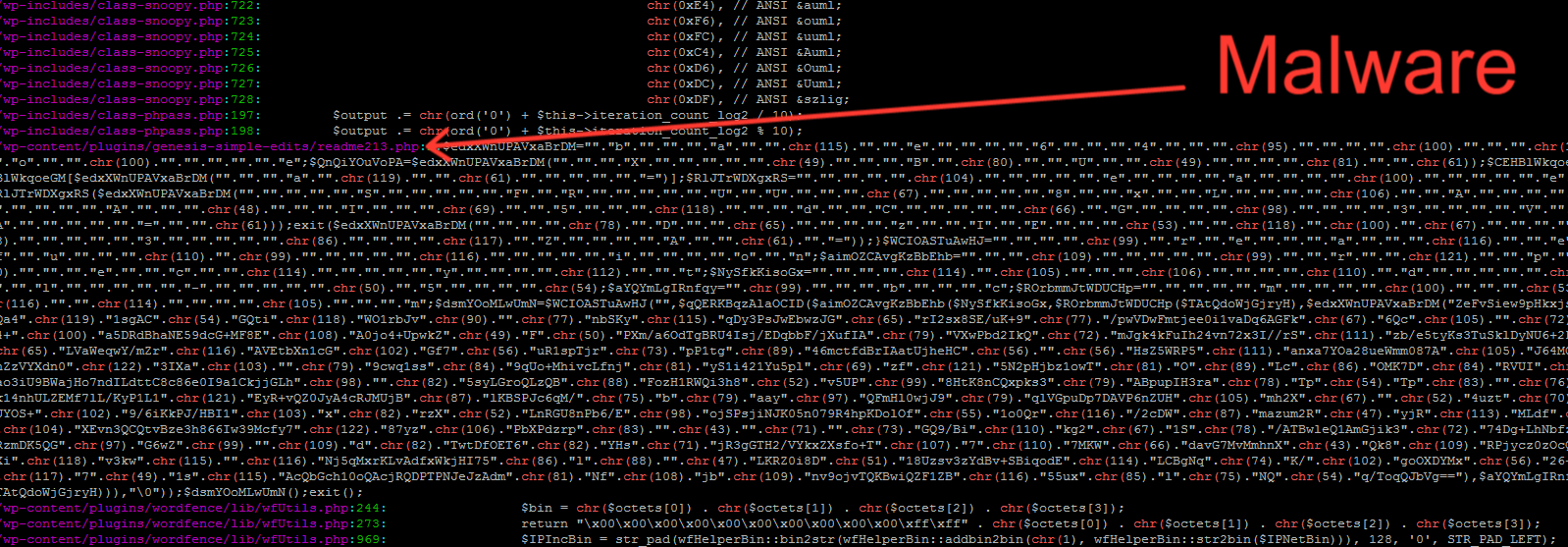
It still missed a few that grep’ing php files looking for excessive usage of chr command that the malware uses to glue strings together to execute the commands using eval that is sent by the hacker via POST and decrypted with base64_decode and html_entity_decode.
Find php files that use chr(..)
grep --color=always -iRnH --include \*.php 'chr(' | more
Find php files that use eval(..)
grep --color=always -iRnH --include \*.php 'eval(' | more
Find js files that use chr(..)
grep --color=always -iRnH --include \*.js 'chr(' | more
Ultimately it would be nice to tweak the command to only detect files with more than N uses char(..). This will help to narrow it down more. Please comment if you have suggestions on how to optimize this grep.
This will still give a lot of false positives. but scrolling through the files, you should at least be able to get an idea.
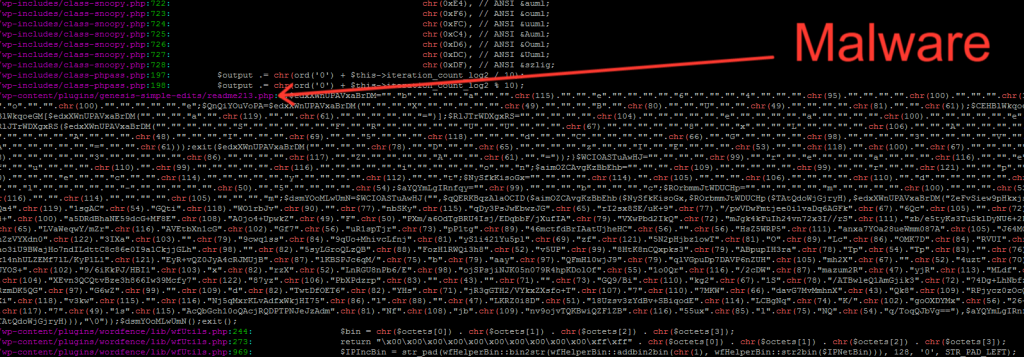
Find file with certain extensions in suspicious folders. (such as /wp-content/uploads_)
cd /wp-content/uploads
find $directory -type f -name "*.php"

Leave a Reply